The digital revolution, indeed, has a profound impact on the healthcare industry, and startups are especially at the forefront. The impact leads to a massive boost in data being generated. Electronic health records, medical imaging files, wearable devices, and data from other sources contribute to its growing landscape. Managing and securing a vast amount of data poses a significant challenge for healthcare startups.
Healthcare is one of the most targeted industries for cybercrime and does not show any sign of slowing down even in 2023. According to the U.S. Government’s OCR (Office for Civil Rights) healthcare firms reported 145 data breaches in the first three months of 2023.
Such attacks can entirely disrupt healthcare systems, cause downtime, and lose patients and other stakeholders. Other factors like massive data volume, variety, interoperability, regulatory compliance, and velocity (as it is updated in real-time), contribute to the complexity of data management and security. Therefore, it becomes vital for healthcare providers to ensure they can seamlessly manage their patient data while enhancing a culture of transparency and trust.
Ensuring robust data security practices not only protects patient information but also secures proprietary data while complying with regulations and maintaining resilience. Read out the blog and find out the key considerations regarding the role of data security in healthcare startups. Also know how implementing appropriate security measures can help.
Key Aspects to Consider for Comprehensive Data Security for Startups
To ensure robust and comprehensive data security in healthcare startups there are three vital aspects that include physical, technical, and procedural security. Here is an overview of each aspect:
1. Physical Security
Physical security covers the measures implemented to protect physical assets, infrastructure, and sensitive information within an organization. It aims to prevent unauthorized access, theft, damage, or disruption to physical resources. Here are some key components of physical security
a. Restricted or Limited Access
With the right measures and implementation of a controlled access system, secure entrances, visitor management protocols, access badges, and biometric authentication systems, organizations can protect their data and control physical access where the data is saved.
b. Surveillance and Monitoring
Surveillance systems and monitoring play a pivotal role in physical security. From the CCTV cameras strategically to monitor activities to a video management system for real-time monitoring and recording the footage helps with physical security. Also installing alarms and alert systems notifies the security personnel of the triggers and takes necessary action to prevent any breach.
c. Equipment and Devices Protection
Safeguarding computer systems to storage devices, hardware, alarms, and secure storage areas can help prevent theft and unauthorized equipment removal.
d. Incident Response and Preparedness
Planning for emergencies like disasters, security breaches, and medical emergencies is another significant area of physical security. Employees must be trained in emergency protocols and conducting drills can help ensure preparedness.
2. Technical Security
Technical security for healthcare startups is about protecting the IT infrastructure and systems to safeguard patients’ and users’ data from unauthorized access and other vulnerabilities. The considerations include:
a. Access Controls
Implementing strong authentication mechanisms, such as passwords, multi-factor authentication, and role-based access control, helps to ensure that only authorized individuals can access sensitive data.
b. Data Encryption
Data encryption converts the patient’s sensitive and confidential information to codes using robust encryption algorithms. It protects the data from unauthorized access and interception. Encrypting data therefore secures whatever is transmitted between the devices and other systems, while ensuring complete protection.
c. Network Security
The healthcare sector relies heavily on network systems to store and transmit patient data. Therefore, deploying firewalls, detection prevention systems, virtual private networks, and encryption technologies to protect network communication and prevent unauthorized access.
d. Secure Code Practices
Secure coding practices cover validating and sanitizing user inputs, implementing the right input/output filtering, avoiding coding pitfalls while staying up to date with the coding practices and guidelines. Implementing secure coding practices in healthcare application development helps to get rid of vulnerabilities and attacks.
e. Protection from Malware
Healthcare startups need to securely update the anti-malware and software that helps detect and prevent any kind of malicious attack.
“Atlantic General Hospital disclosed that a January ransomware attack tied to reported IT outages also potentially impacted the PHI (Personal Health Information) of over 30,000 patients.”- Tech Target.
Malware like viruses and spyware, ransomware can cause significant harm. Therefore, protection from malware helps detect and remove it, preventing its spread.
3. Procedural Security
Healthcare startups must prioritize procedural security to ensure the smooth operation of their services, protect patient privacy, and mitigate operational risks. Here are some of the important procedural considerations:
a. Security Policies
Security policies offer a framework for defining healthcare organization approach toward data security. Implementing comprehensive security policies in place that highlight the important guidelines, practices, and standards that set clear expectations and a unified approach towards healthcare data protection.
b. Employee Training and Awareness
Employee awareness and conducting regular security training sessions educate them about the risks, policies, best guidelines, practices, and a lot more to ensure confidentiality and compliance in healthcare. The programs educate employees on their roles and responsibilities in maintaining data security, privacy, and compliance.
c. Regular Audits and Assessments
Conducting security audits, vulnerability assessments, and penetration tests identifies the weaknesses, assesses compliance, and addresses the security gaps and vulnerabilities.
d. Vendor Management
Includes establishing the right process for vendor management. It includes due diligence while selecting the vendors, assessing their capabilities, and ensuring that the right contract is in place for protecting patient data. Monitoring and auditing vendors’ security practices help mitigate the risks and protect data from third parties.
Challenges that Need to be Addressed the Right Way
There are several challenges startups face to ensure data security in healthcare and addressing them is vital. Let us put some light on each one of them:
High Cost
Implementing security measures in healthcare can be a costly affair, especially for startups (they have limited financial resources). As healthcare organizations need to invest in such technologies, infrastructure, and maintenance, balancing the need for robust security measures needs clear practices, planning, and prioritization.
Hiring Organization with Right Expertise
Finding the right talent and building a team with expertise in healthcare is yet another challenge. Ensuring data security in healthcare needs knowledge of the industry, best practices, and threat management. Startups may face difficulty in finding experienced professionals or vendors they can rely on.
Scaling Security as the Startup Grows
As healthcare startups grow, there is a rapid evolution of their operations, customer base, and infrastructure. Scaling security measures to manage growth can be challenging for organizations. Therefore, assessing the security needs regularly and adopting strategies that can be integrated with the existing infrastructure securely can help address the challenge.
Regulatory Compliance
There are various data protection regulations like HIPAA (Health Insurance Portability and Accountability), GDPR (General Data Protection Regulation), and others. Ensuring compliance with these regulations may make security efforts complex. Therefore, healthcare organizations need to understand their obligations and implement appropriate security measures to meet standards.
How can Healthcare Startups Manage their Data Security Seamlessly
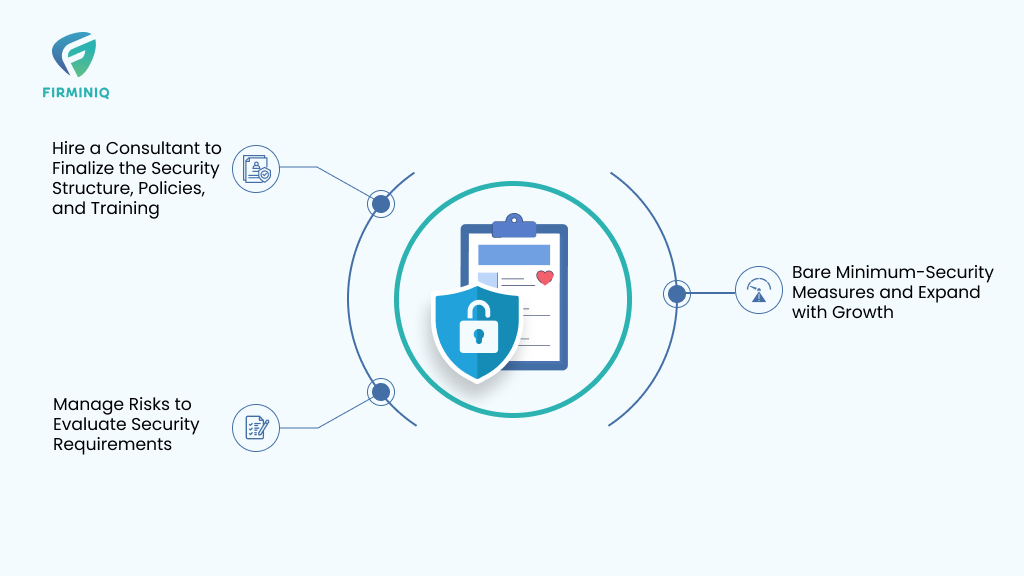
Healthcare startups can seamlessly manage their data security with a comprehensive and proactive approach. Know the key aspects that can help ensure data security:
Hire a Consultant to Finalize the Security Structure, Policies, and Training
Hiring an experienced consultant or organization can offer healthcare organizations the guidance they need for growth and setting up a robust healthcare data security structure. By assessing the existing system and identifying vulnerabilities, the consultant can help with the right security measures. An experienced consultant can even help healthcare organizations with comprehensive policies and procedures for data handling, and incident response, and offer employee training.
The consultant with expertise in healthcare data security ensures that the organization’s security aligns with industry best practices and has knowledge of regulations like HIPAA.
Manage Risks to Evaluate Security Requirements
Healthcare organizations must be able to identify risks and manage them to determine security requirements. From conducting regular risk assessments to identifying the vulnerabilities and threats, and technology infrastructure, the consultant should primarily prioritize risks based on their potential impact and occurrence. By having a clear understanding of such scenarios, healthcare organizations can allocate resources accordingly and address the concerns as per their priority.
Bare Minimum-Security Measures and Expand with Growth
When it is about data security for startups, beginning with bare minimum-security measures and expanding globally as the organization grows is vital. In simple terms, organizations should begin by implementing foundational data security measures that address the most critical risks and compliance requirements.
This approach helps with establishing a robust foundation and avoids complexity. Beginning with implementing fundamental security controls like robust access control, backups taken regularly, and security awareness training regularly can help healthcare organizations.
As the organization expands, it can add more sophisticated security measures, such as intrusion detection and prevention systems, Security Information and Event Management (SIEM) solutions, and advanced threat detection technologies. Continuously monitoring and reassessing security measures helps to adapt to evolving threats and technological advancements. Some of the aspects to consider are:
a. Start with Data Security Aspects
Organizations should consider data security aspects including patient privacy, compliance, breach prevention, Intellectual Property protection, and others to ensure continuity.
b. Based on Architecture/ Customer Profile Network
Organizations should offer tailored security measures based on the startup’s IT infrastructure architecture and nature of the customer profile network. Different customer profiles have varying security requirements, so customizing them as per the need can help.
Epilogue
Data security measures and implementation strategies in healthcare startups can be customized as per the organization’s need, architecture, network, and more. Consulting the right data security service professionals can help set up a secure and scalable cloud-enabled healthcare setup.
Do you wish to leverage our understanding and our expertise on HIPAA and other privacy regulations to build healthcare solutions that protect patient data? Reach out to FIRMINIQ today!
We would love to hear your feedback! Please let us know in the comments section below. We value your opinion and appreciate your time in sharing your thoughts.