Introduction
As healthcare continues to transform and improve, remote patient monitoring is becoming popular among clinicians and patients. While the benefits of RPM (Remote Patient Monitoring) are already known, one of the critical challenges organizations face is ensuring the security and privacy of patient data.
Securing patient data and vital information in RPM needs a comprehensive approach to compliance. As there is a constant flow of data, clinicians need to ensure that they are equipped with patient’s health information and keep it safe. Compliance in RPM has various regulations like HIPAA (Health Insurance Portability and Accountability) in the USA, GDPR (General Data Protection Regulation) in European countries and other specifications as per different countries.
Fortified Health Security’s mid-year report stated that the healthcare sector suffered 337 breaches in the first half of 2022 alone. As there is a rapid shift and focus on RPM and telehealth by healthcare organizations, the breaches rise, and it becomes vital for the healthcare organizations to follow the best regulatory guidelines and practices.
Well, for more clarification on the same, here is a comprehensive blog that outlines the key considerations that help with secure data transmission in RPM and help maintain compliance.
Key Considerations that Help Maintain Compliance in RPM
Maintaining compliance in remote patient monitoring is vital for the healthcare organizations that protect patients’ data, their privacy and ensure regulatory requirements are met. Here are the key considerations that helps you maintain compliance:
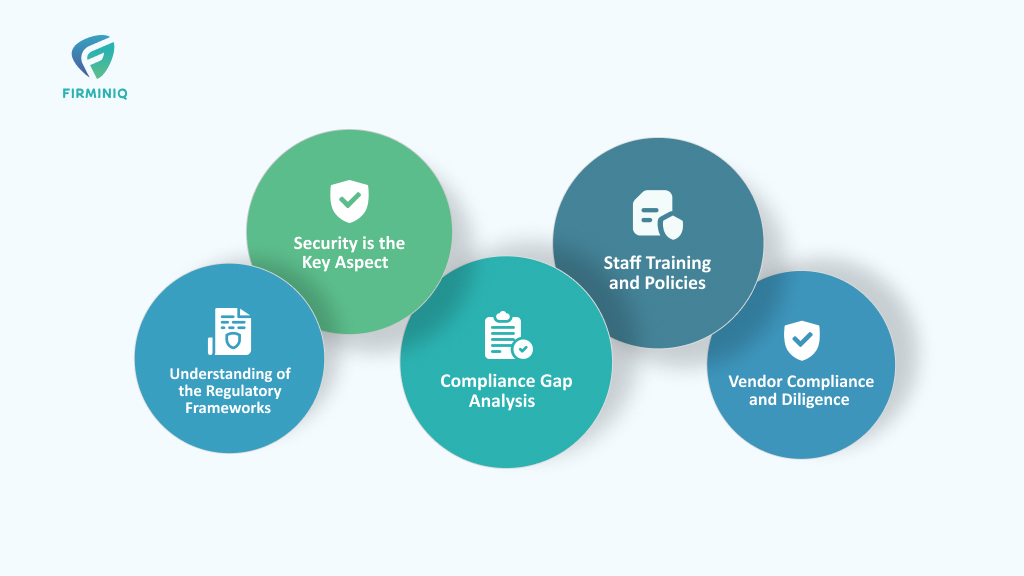
1. Understanding of the Regulatory Frameworks
Healthcare organizations should be aware of and understand several regulations like HIPAA, GDPR and other laws as per the location. Staying up with all the regulatory frameworks helps maintain privacy, security, and ethical standards in remote patient monitoring. Here we focus on some of the regulatory framework’s organizations should focus on:
a. Health Insurance Portability and Accountability Act (HIPAA)
A popular healthcare regulation in the US that governs the security and privacy of sensitive patient health information and prevents it from being disclosed without the patient’s consent or knowledge.
b. General Data Protection Regulation (GDPR)
It is one of the toughest privacy and security laws that applies to organizations operating in European countries. It aims to give patients control over their own personal data by holding the healthcare organizations responsible for the way they handle and use the information. If RPM involves data of EU patients, compliance with GDPR is essential.
c. Medical Device Regulations
RPM involves the usage of medical devices like sensors, wearables, and equipment. Therefore, compliance with various medical devices regulations is crucial to ensure the device’s safety and quality.
d. Data Security Standards
Adhering to recognized data security standards is essential to ensure the safeguarding of patient data, protecting patient privacy, and maintaining an environment free of threats. ISO/IEC 27001 and NIST Cybersecurity Framework are a few of the widely recognized security standard frameworks that help mitigate the data security risks.
e. Reimbursement and Health Insurance Regulations
Reimbursement and insurance regulations help understand the billing policies, procedures, and compliance with specific requirements to receive the reimbursement. Ensuring that the provider or coding experts are aware of the frequently used codes for billing.
2. Security is the Key Aspect
Ensuring data security in healthcare has always been a pivotal and challenging task.
The lack of poor implementation of data security in healthcare makes it more vulnerable for hackers to attack. Also, RPM uses a variety of technological devices that connect physicians and patients. The complex setup and data transmission in real-time enhances the risk for cyberattacks.
Therefore, implementing robust data security measures like data encryption (both in rest and in transit), secure and two-factor user authentication, security patches and regular updates, role-based access and other practices helps ensure security.
3. Compliance Gap Analysis
Compliance gap analysis refers to a process where the organization’s current state of compliance with the laws, regulations, and standards are identified, to determine whether they align with the requirements that apply to its operations.
So, to ensure compliance, a proper analysis helps evaluate the RPM processes and policies to identify the gaps in the system and deficiencies. The analysis involves data privacy assessment, security control, documentation, and other vital areas. Identifying the areas and filling in the gap analysis will help meet the compliance standards.
4. Staff Training and Policies
Offering staff training and implementing robust policies in place is vital for all the stakeholders involved in remote patient monitoring. From training on data privacy to relevant regulations and standards like HIPAA, GDPR, and others to access control and authentication, educating the staff on these vital topics is the key to success.
Also, developing and enforcing policies and procedures that address data handling, incident response, ethical considerations, and employee responsibilities is a part of staff training.
5. Vendor Compliance and Diligence
When you hire a third-party vendor for remote patient monitoring, thoroughly assessing the vendor with all the compliance and regulatory requirements is vital for protecting patient data. From evaluating vendors based on frameworks to data security measures, to evaluating their reputation helps mitigate potential risks associated with outsourcing RPM services.
Therefore, conducting due diligence for vendor compliance helps organizations ensure the RPM solution provider meets all the necessary standards.
Also, if you are confused about whether to build or buy an RPM solution, here is our blog that can help.
Buy or Build Remote Patient Monitoring Solution? How to Filter the Noise from the Signal
Conclusion
In the healthcare sector, securing patient data is most important and it requires a comprehensive approach to compliance. A clear understanding of regulatory frameworks, robust data security measures, due diligence for vendor compliance, and staff training help ensure privacy, security, and patient data integrity throughout the RPM.
Following these best practices and staying informed about emerging trends and technologies, healthcare providers can continue to leverage the benefits of RPM while safeguarding patient data. If you are looking for remote patient monitoring services without worrying about the compliance regulations, reach out to us!