In mobile app development, user authentication is a critical aspect to ensure the security and integrity of user data. Two popular authentication mechanisms that developers often encounter is OAuth (Open Authorization) and JWT (JSON Web Token). This blog will delve into the intricacies of these technologies, providing insights into their functionalities, use cases, and the advantages they bring to the table.
Understanding OAuth
OAuth, which stands for Open Authorization, is an industry-standard protocol that allows secure third-party access to user’s data without exposing their credentials. It is widely used for delegated access scenarios, where a user can grant limited access to their resources to another application or service. OAuth operates by exchanging tokens, typically in the form of access and refresh tokens, to facilitate secure communication between different entities.
Key features of OAuth include:
- Delegated Authorization
- Token-Based Authentication
- Refresh Token Mechanism
The OAuth Flow
OAuth is commonly used in mobile apps to facilitate secure and authorized access to protected resources, APIs, or user data without exposing the user’s credentials. Mobile app developers often integrate OAuth to enable seamless and secure authentication and authorization processes.
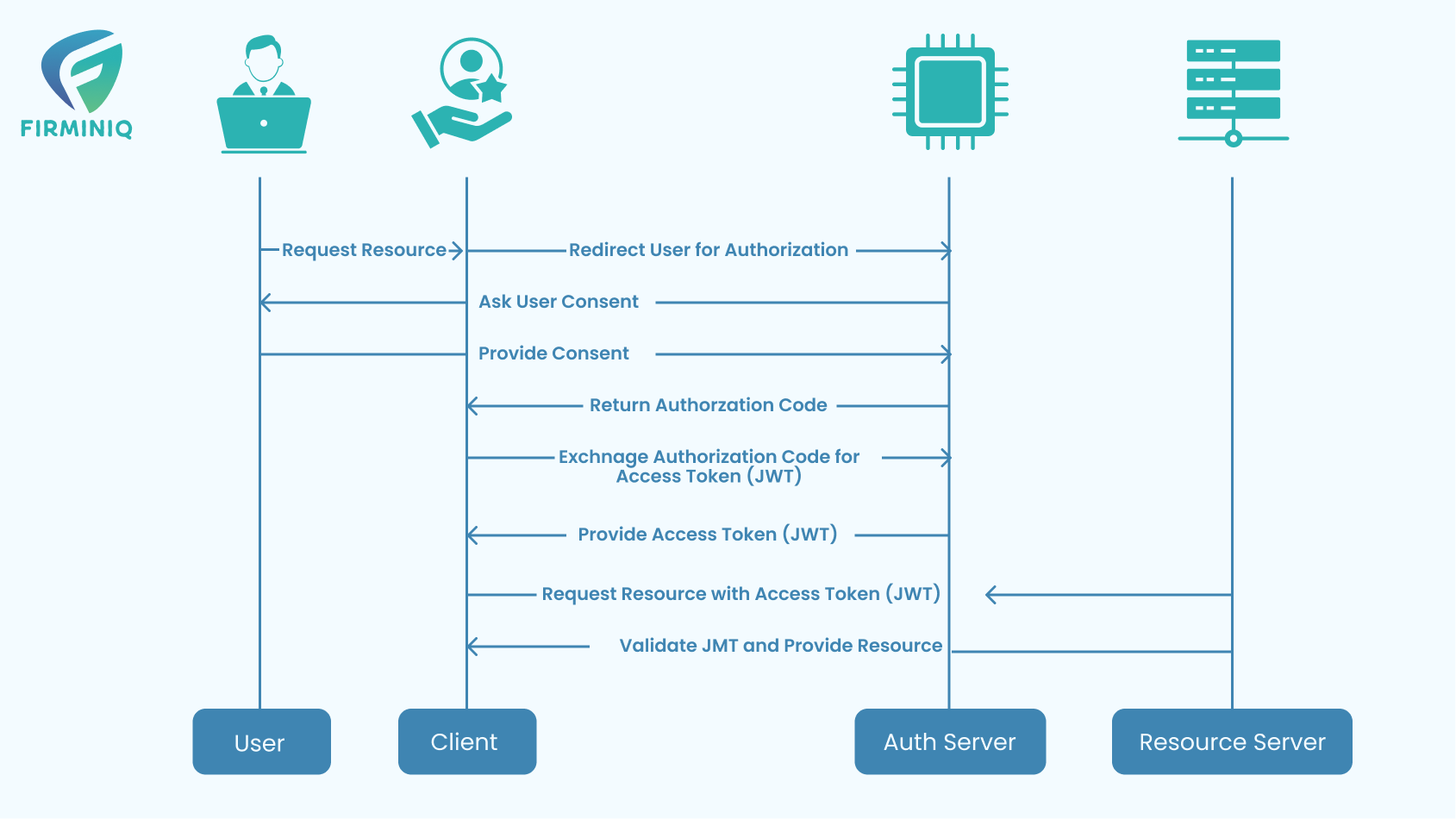
Understanding the OAuth flow is crucial for implementing secure authentication in mobile apps. The typical OAuth flow involves several steps, including authorization request, user authentication, and token exchange. This section will provide a step-by-step breakdown of the OAuth 2.0 authorization process, shedding light on each phase’s role in ensuring a robust and secure authentication mechanism.
Here’s how OAuth flow is typically implemented in mobile apps:
1. User Authentication
a. When a user attempts to log in or access a protected resource within a mobile app, the app initiates the OAuth authentication flow.
b. The app redirects the user to the authorization server (such as a social media platform or identity provider) for authentication.
2. Authorization Request
a. The mobile app sends an authorization request to the authorization server, specifying the requested permissions (scopes) and the type of access (read, write, etc.).
b. The user may be prompted to log in and grant the app permission to access their resources.
3. Authorization Grant
a. Upon successful authentication and user consent, the authorization server issues an authorization grant to the mobile app. The grant represents the user’s permission for the app to access specific resources.
4. Token Request
a. The mobile app uses the authorization grant to request an access token from the authorization server.
b. Additionally, the app may request a refresh token, which can be used to obtain a new access token without requiring the user to re-authenticate.
5. Token Issuance
a. The authorization server validates the authorization grant and issues an access token (and possibly a refresh token) to the mobile app.
b. The access token is a bearer token that the app can include in API requests to access protected resources.
6. API Access with Access Token
a. The mobile app includes the access token in the authorization header of API requests when accessing protected resources on behalf of the user.
b. The resource server (API) validates the access token to ensure the app has the necessary permissions.
7. Token Expiration and Refresh
a. Access tokens typically have a limited lifespan. When an access token expires, the mobile app can use the refresh token to obtain a new access token without requiring the user to re-enter credentials.
8. Secure Storage and Handling
a. Mobile apps need to securely store and handle access tokens. This often involves using secure storage mechanisms and implementing proper security measures to protect tokens from unauthorized access.
Understanding JWT
JWT, or JSON Web Token, serves as a concise and URL-safe method for conveying claims between two parties, predominantly employed for authentication and authorization purposes. Comprising three integral parts, JWTs provide a structured approach to information transfer:
Header
This component typically comprises two segments, specifying the token type (JWT) and the utilized signing algorithm, such as HMAC SHA256 or RSA.
Payload
The second facet of the token, the payload, encompasses the claims. These claims serve as statements about an entity, often the user, accompanied by additional data. Usually, these claims are of the type – registered, public, and private.
Signature
Crafting the signature involves taking the encoded header, the encoded payload, a secret, the algorithm specified in the header, and signing the combination. The resulting JWT is a string that seamlessly traverses between parties. Its digital signature ensures integrity, instilling trust in the contents for the receiving party.
The JWT Flow
In mobile authentication, JSON Web Tokens (JWTs) are often used as part of the authentication flow to securely transmit information between the mobile app and the server. The typical JWT flow in mobile authentication involves the following steps:
1. User Registration or Login
When a user registers or logs into the mobile app, their credentials (such as username and password) are sent securely to the server.
2. Authentication on the Server
The server verifies the credentials and, if valid, generates a JWT containing relevant information about the user (claims) and any additional metadata.
3. JWT Generation
- The server creates a JWT by combining three parts: the header, payload, and signature.
- The header includes token type and the signing-algorithm.
- The payload contains claims, such as user ID, username, expiration time, and any other relevant information.
- The signature is generated by signing the concatenated header and payload with a secret key using the specified algorithm.
4. Sending JWT to the Mobile App
The server sends the generated JWT back to the mobile app as part of the authentication response.
5. JWT Storage on the Mobile App
The mobile app securely stores the JWT, typically in a secure storage mechanism (e.g., Keychain on iOS, Keystore on Android).
6. Subsequent Requests with JWT
For subsequent requests to protected resources on the server (e.g., accessing user-specific data or performing actions), the mobile app includes the JWT in the request headers.
7. JWT Verification on the Server
- The server receives the JWT in the request headers and verifies its authenticity by checking the signature using the secret key.
- The server also checks the claims within the payload, such as expiration time, to ensure the token is still valid.
8. Authorization and Response
- If the JWT is valid, the server authorizes the request and processes it accordingly.
- If the JWT is expired or invalid, the server may respond with an error, and the mobile app may need to be re-authenticated.
This flow provides a secure and efficient way to handle user authentication and authorization in mobile applications, allowing the server and the mobile app to communicate securely and share information about the user’s identity.
Enhancing Mobile App Security: OAuth 2.0 along with JWT
“Integrating OAuth 2.0 with JWT for Authentication and Authorization” refers to the practice of combining two widely used technologies, OAuth 2.0 and (JWT), bolster the security of mobile applications during the processes of user authentication and authorization.
Integrating OAuth along with JWT in a mobile application involves several steps to ensure secure and effective authentication and authorization. Below are the general steps:
1. Set Up OAuth 2.0 Provider
Choose an OAuth 2.0 provider or set up your own authorization server. This server will handle authentication, authorization, and token issuance. Popular providers include Google, Facebook, or you can use open-source solutions like Auth0.
2. Register Your Mobile App
Register your mobile app with the OAuth provider to obtain client credentials (client ID and client secret). This registration helps the provider identify and authenticate your app.
3. Implement OAuth Authorization Flow
Choose an OAuth 2.0 flow suitable for mobile apps. The Authorization Code Flow is commonly used. In this flow:
- Redirect users to the authorization endpoint of the OAuth provider.
- Users log in and grant permissions.
- The OAuth provider redirects back to your app with an authorization code.
4. Exchange Authorization Code for Tokens
Use the obtained authorization code to request access and refresh tokens from the OAuth provider’s token endpoint. These tokens will be used for authenticating API requests.
5. Use JWT as Access Token
Optionally, configure the OAuth provider to issue JWTsas access tokens. JWTs are self-contained and can include user claims, reducing the need for additional requests to fetch user information.
6. Securely Store Tokens on Mobile Device
Store tokens securely on the mobile device by using Keychain on iOS or the Keystore on Android. This helps prevent unauthorized access to tokens.
7. Include JWT in API Requests
When making requests to secure APIs, include the JWT (access token) in the Authorization header. This allows the API to verify the user’s identity and authorization.
8. Handle Token Expiration and Refresh
Implement logic to handle token expiration. Use the refresh token to obtain a new access token without requiring user reauthentication. This ensures a seamless user experience.
9. Implement Token Revocation (Optional)
Optionally, implement token revocation logic. If a user logs out or revokes access, communicate with the OAuth provider to invalidate tokens.
10. Security aspects
Ensure that the communication between your mobile app and APIs is secure by using HTTPS for preventing man-in-the-middle attacks. Keep your OAuth library, JWT library, and other dependencies up to date to benefit from security patches and improvements.
Conclusion
In conclusion, the choice between OAuth and JWT for user authentication in mobile apps is a nuanced decision that depends on various factors such as security requirements, scalability, and the specific use case of the application. Both OAuth and JWT offer distinct advantages and trade-offs. OAuth excels in providing a standardized and secure authorization framework, making it suitable for scenarios where third-party access is a key consideration. On the other hand, JWT, with its stateless nature and compact structure, is advantageous for scenarios that prioritize simplicity and speed. Ultimately, developers must carefully assess their app’s needs and the specific context of user authentication to make an informed decision.