Securing data within AWS (Amazon Web Services) remains pivotal in an age where cyber threats loom large. Understanding the challenges and solutions within AWS security is paramount. From misconfigurations to access control complexities, compliance issues, and evolving threats, businesses face a multitude of obstacles. Let’s delve into these challenges and explore viable solutions to fortify AWS security effectively.
AWS Security Challenges
1. Configuration Management
Making sure that all configurations are set up and kept up to date is one of the biggest issues with AWS security. A misconfigured configuration can expose the company to attack and jeopardize confidential information.
2. Access Control
It can be difficult to control user access to Amazon resources, especially when dealing with multiple users and external services. Making sure users only have access to the resources they require and that those permissions are routinely reviewed and updated.
3. Compliance
There are numerous industries with specialized laws governing privacy and data protection. Businesses must make sure their AWS security measures are up to date and compliant, and AWS security must adhere to these rules.
4. Visibility
Getting a complete picture of an organization’s AWS security posture might be difficult. This can make it challenging to identify security concerns and appropriately assess risks.
5. Advanced Threats
Advanced dangers including malware, phishing scams, and other cybercriminal techniques must be addressed by Amazon security. Companies must check their AWS security carefully and take prompt action in the event of any suspicious behavior.
Ultimately, overcoming these obstacles necessitates a proactive and continuing approach to AWS security, with an emphasis on ongoing education and training, regular updates, and continual monitoring. Businesses can improve the security of their sensitive data and information in the cloud by addressing these issues.
Options and Solutions, with Pros and Cons
Businesses have a variety of alternatives and solutions to choose from when it comes to AWS security. Here are some of the more popular methods, along with their benefits and drawbacks:
1. Workspace
We are utilizing an AWS Workspace to access AWS resources. This workspace is extremely secure because no one else can access AWS services from it. Within Workspaces, Internet access is restricted, and the data is extremely safe.
Pros: Workspace can give users a safe atmosphere in which to conduct business.
Cons: Working within the workspace might be difficult because of numerous limits, including copy/paste restrictions and the workspace locking automatically if someone is not working. Access to the internet is also limited.
2. Access Control
Managing user access to AWS resources is the practice of access control. This can involve assigning users rules and rights, putting multi-factor authentication into place, and often checking and upgrading access controls.
Pros: Robust access control can stop unauthorized access to confidential information and resources.
Cons: Managing access controls for extensive and complicated AWS setups can be difficult. It can be time-consuming and resource-intensive, and it necessitates continual monitoring and changes.
3. Network Security
Securing network traffic both within and between AWS environments is a component of network security. This may entail setting up firewalls, installing intrusion detection and prevention tools, and keeping an eye on network traffic for unusual activity.
Pros: Strong network security may shield users from hazards like malware and phishing attempts and prevent unwanted access.
Cons: Implementing and managing network security can be challenging, especially in expansive and intricate AWS systems. It might be resource-intensive and necessitate continual monitoring and updating.
4. Encryption
Encryption includes encrypting data so that only authorized individuals can access it. Amazon offers both server-side and client-side encryption as well as other encryption solutions.
Pros: Data can be protected from illegal access via encryption, which also adds another layer of security for sensitive data.
Cons: Performance may suffer, and encryption may consume a lot of resources. Also, difficult and requiring continual monitoring and changes is managing encryption keys.
5. Monitoring and logging
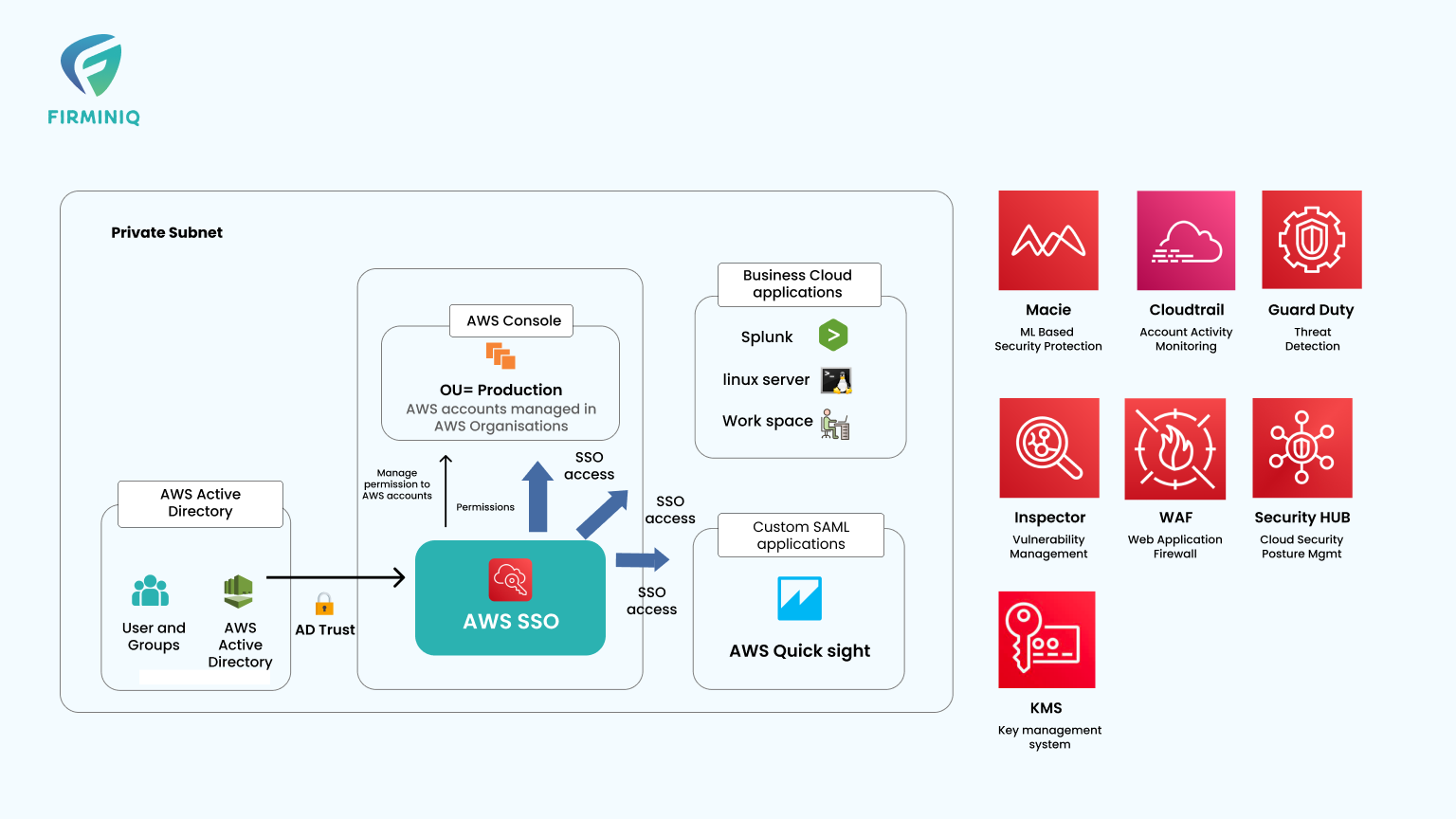
This entails routinely reviewing and examining AWS logs and keeping an eye out for unusual activities. We make use of CloudTrail, AWS CloudWatch, and Splunk.
Pros: Quick detection and action can be taken in response to security threats in order to prevent serious harm.
Cons: Monitoring and logging can consume a lot of resources and produce a lot of data, necessitating a lot of storage space and computing power. It also needs to be monitored and updated continuously.
6. Single Sign On (SSO)
SSO entails controlling user identities and access to AWS resources, including the establishment of rules and restrictions as well as the administration of roles and groups.
Pros: A strong SSO can guard against unwanted access and guarantee that users have access to only the resources they require.
Cons: SSO setup and management can be challenging, especially in expansive and intricate AWS setups. It might be resource-intensive and necessitate continual monitoring and updating.
Overall, each of these options and approaches to solutions can help to strengthen Amazon security. But each strategy has a unique mix of benefits and drawbacks, so businesses must carefully weigh their security requirements and available resources to decide which strategy—or group of strategies—is ideal for them.
Conclusion
In the dynamic landscape of AWS security, businesses encounter multifaceted challenges. However, proactive measures and strategic solutions pave the way for enhanced protection. Options such as Workspace utilization, robust Access Control, Network Security implementations, Encryption methodologies, Monitoring & Logging tools, and Single Sign-On systems each present unique strengths and limitations. The crux lies in meticulously aligning these solutions with organizational security needs and resource capacities. By embracing a tailored approach, businesses can bolster their AWS security posture, fortify sensitive data, and navigate the ever-evolving threat landscape with resilience and confidence. As a trusted cloud partner, we specialize in AWS Cloud services, ensuring your business stays protected and resilient in the face of emerging threats. Get in touch to know more.