HIPAA Compliance Overview for Organizations
Determining HIPAA Applicability
To achieve HIPAA compliance, the first step is determining if your organization is subject to the Administrative Simplification provisions of the Health Insurance Portability and Accountability Act (HIPAA). If your organization falls under these provisions, it is important to identify which specific provisions apply.
Identifying HIPAA-Covered Entities, Business Associates, and Workforce Members
Covered Entities
Covered Entities are organizations that must comply with all Administrative Simplification provisions of HIPAA. This generally includes health plans, healthcare clearinghouses, and healthcare providers that electronically transmit health information in relation to HIPAA-regulated transactions. However, there are exceptions, such as health plans providing excluded benefits or on-campus health centers that serve only students.
Business Associates
Business Associates are entities that perform services for or on behalf of Covered Entities involving Protected Health Information (PHI). While they are not subject to all HIPAA provisions, Business Associates must comply with specific rules, such as the Security Rule and Breach Notification provisions.
Workforce Members
Individuals under the direct control of Covered Entities or Business Associates, regardless of payment, must comply with relevant HIPAA provisions through established organizational policies and procedures.
Determining HIPAA Applicability Checklist
To determine if your organization is subject to HIPAA’s Administrative Simplification provisions, consider the following questions:
- Is your organization a provider of health plans, HMOs, Medicare supplemental policy issuers, or involved in federal/state-funded health programs?
- Is your organization a healthcare clearinghouse, billing service, repricing company, or is it involved in health information processing activities?
- Does your organization transmit health information electronically in connection with HIPAA-regulated transactions?
- Does your organization create, receive, maintain, or transmit PHI for or on behalf of a Covered Entity?
- Is your organization a health information organization, e-prescribing gateway, or a provider of data transmission/storage services for PHI?
- Does your organization provide subcontractor services involving PHI?
If any of these criteria apply, your organization is a Covered Entity or Business Associate, and compliance with relevant HIPAA provisions is required.
HIPAA Privacy Rule Checklist
The HIPAA Privacy Rule protects the privacy of individuals’ medical records and PHI. Key requirements include:
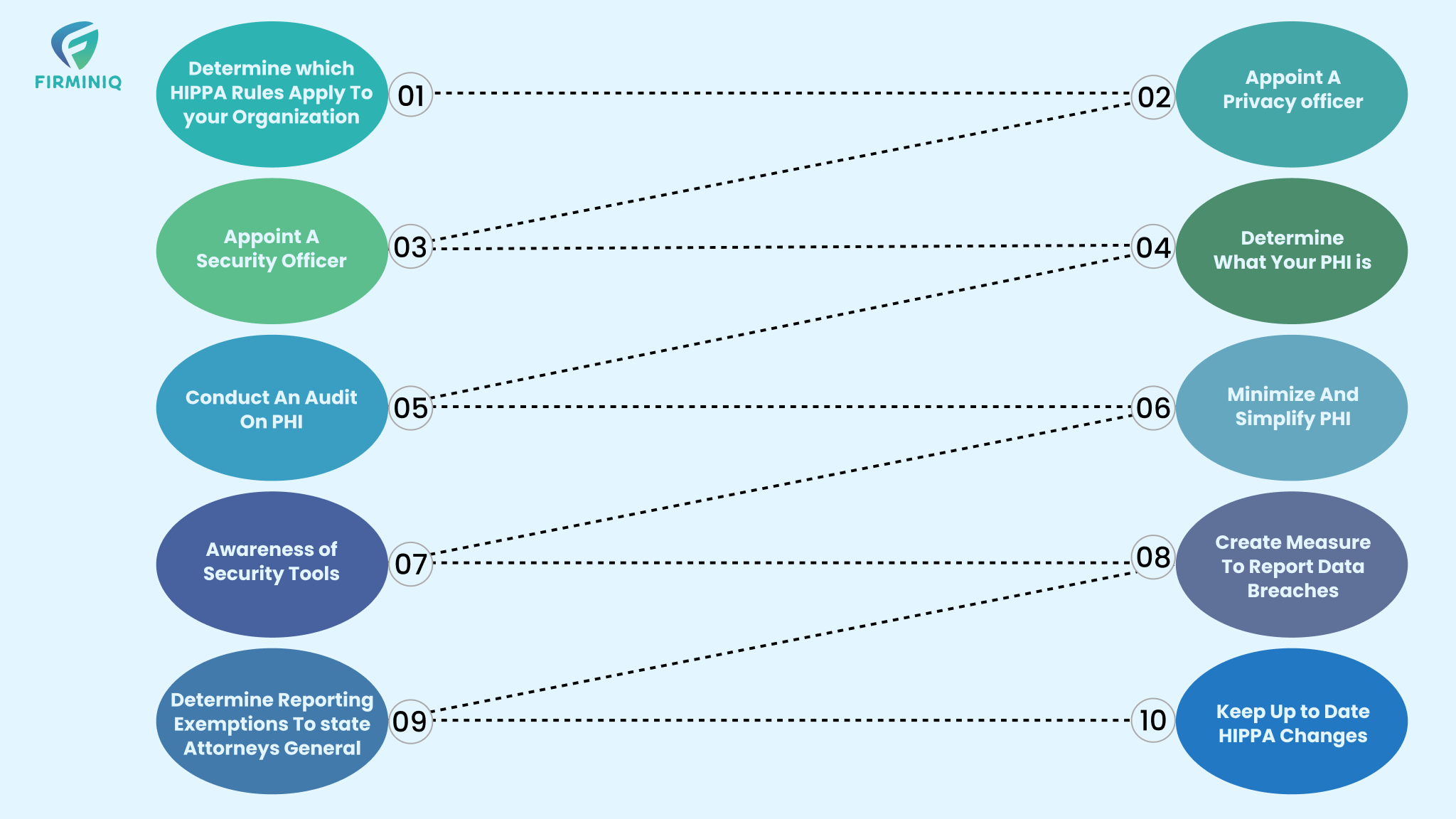
- Appointing a HIPAA Privacy Officer responsible for policy development and enforcement.
- Understanding the rules for PHI usage, disclosures, and obtaining authorizations.
- Identifying and mitigating privacy risks to a reasonable level.
- Developing policies and procedures for PHI use, disclosure, and authorization.
- Distributing a Notice of Privacy Practices outlining PHI usage and individual rights.
- Managing patient requests for access, correction, and data transfer.
- Establishing breach reporting procedures and training the workforce.
- Implementing sanctions policies for non-compliance.
- Ensuring due diligence on Business Associates and maintaining agreements.
- Developing a contingency plan for emergencies affecting PHI.
By adhering to these guidelines, organizations can ensure HIPAA compliance and effectively protect sensitive health information.
Importance of the HITECH Act
The Health Information Technology for Economic and Clinical Health (HITECH) Act is crucial for the healthcare industry, as it drives the shift from paper to digital medical records. It also enhances the HIPAA Privacy and Security Rules concerning Electronic Health Records (EHRs) by introducing security audits for healthcare providers.
Before discussing the significance of the HITECH Act, it’s important to understand HIPAA’s limitations:
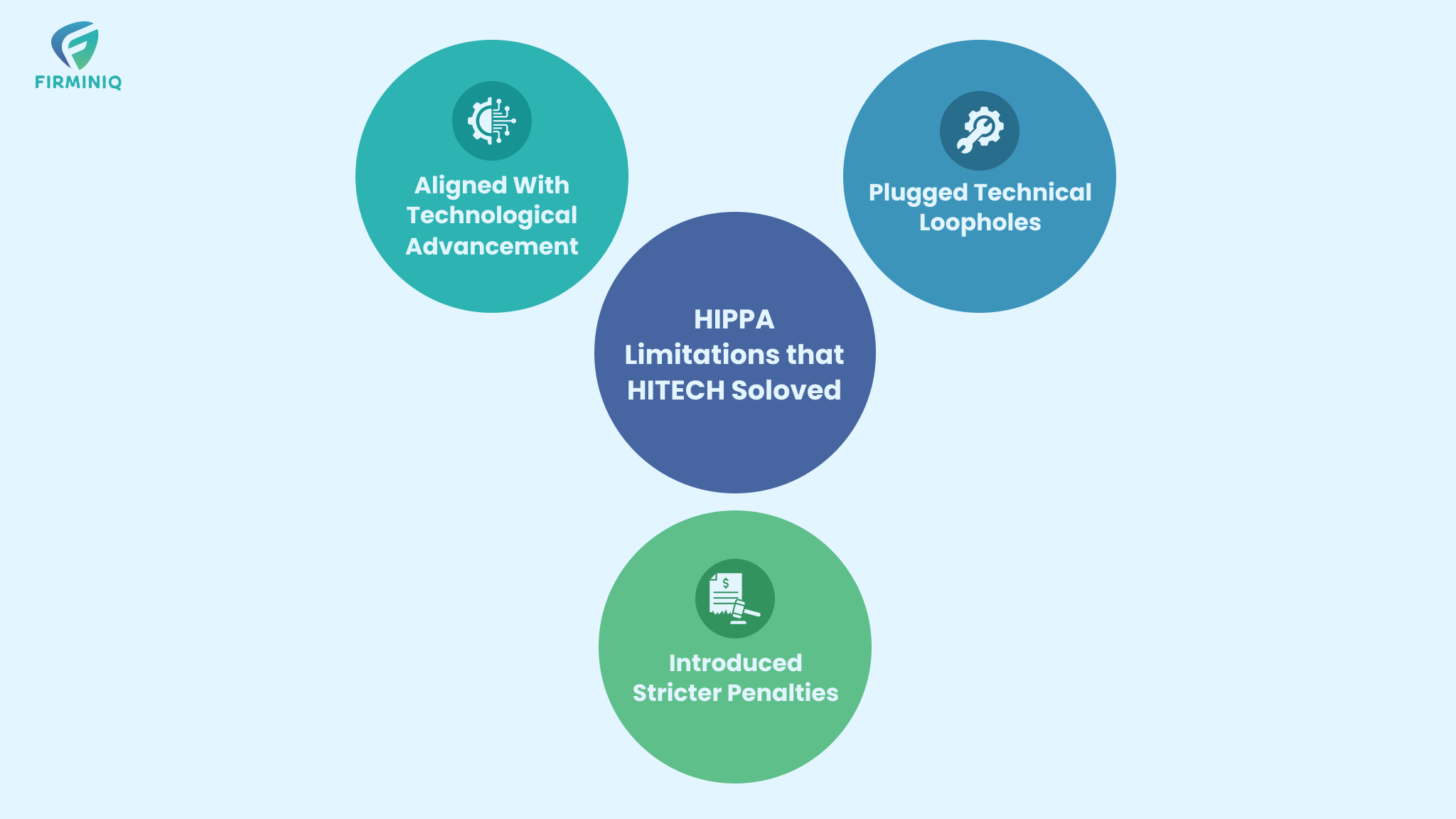
- Technological Misalignment: HIPAA, established in 1996, predates the widespread digitization that has transformed industries and daily life. Consequently, HIPAA lacked adequate provisions to effectively regulate the security and privacy of electronic health information.
- Technical Loopholes: HIPAA did not impose comprehensive accountability on business associates of HIPAA-covered entities for data security and privacy. Third-party vendors with access to Protected Health Information (PHI) often maintained lower security standards and faced minimal liability for breaches.
- Lenient Penalties: HIPAA non-compliance penalties were relatively modest, lacking sufficient deterrence to prompt healthcare organizations to enhance their security measures. The maximum fine under the 1996 HIPAA Act was $25,000, with typical penalties averaging around $100 per violation.
The HITECH Act addressed these shortcomings by building upon HIPAA and enacting stricter regulations to hold third-party associates of HIPAA-certified organizations accountable for compliance. It mandated data breach notifications to patients or health plan members affected by breaches.
The HITECH Act is structured into four categories
- Promotion of Health Information Technology: This section focuses on establishing an electronic healthcare infrastructure, encouraging the adoption of EHRs, and implementing relevant standards.
- Testing of Health Information Technology: It defines eligibility criteria for entities to apply for grants and funding to participate in testing healthcare delivery and information technologies.
- Grants and Loans Funding: This subtitle outlines the utilization of grant and loan funds, oversight mechanisms to ensure proper utilization, and compliance standards for health information technologies.
- Privacy: This section enhances security and privacy provisions, clarifies their relationship with other laws, and stipulates effective dates. It extends regulatory standards to non-HIPAA-covered entities, ensuring consistent compliance across the healthcare landscape.
Purpose of the HITECH Act
The Health Information Technology for Economic and Clinical Health (HITECH) Act serves multiple purposes within the US healthcare system, aiming to enhance safety, quality, efficiency, care coordination, patient engagement, population health, and data security and privacy.
Key objectives and purposes of the HITECH Act include:
- Encouraging EHR Adoption: The Act incentivizes healthcare providers to transition from paper-based records to EHR systems, aiming to modernize healthcare information management and improve accessibility and interoperability.
- Addressing HIPAA Loopholes: The HITECH Act closes loopholes in the Health Insurance Portability and Accountability Act (HIPAA), particularly concerning the accountability of Business Associates of covered entities for safeguarding Protected Health Information (PHI).
- Business Associate Compliance: It mandates that Business Associates of HIPAA-covered entities comply with HIPAA rules and regulations, ensuring a comprehensive approach to data security and privacy across the healthcare ecosystem.
- Data Breach Notifications: The Act requires healthcare organizations to notify patients when their PHI is compromised in a data breach, enhancing transparency and empowering individuals to take necessary actions to protect their privacy.
- Enforcement of Penalties: The HITECH Act imposes more prohibitive penalties for HIPAA non-compliance, including tiered penalties based on the severity and duration of violations, aiming to incentivize organizations to prioritize data security and privacy.
- Improving Healthcare Quality and Efficiency: By promoting the adoption of EHR systems and strengthening data security measures, the Act aims to enhance the quality, safety, and efficiency of healthcare delivery, ensuring that patient information is managed securely and effectively.
Purpose of the HITECH Act
The Health Information Technology for Economic and Clinical Health (HITECH) Act aims to enhance the healthcare system by improving safety, quality, and efficiency; increasing coordination of care; engaging patients in their healthcare; improving the overall health of the population; and ensuring the security and privacy of health information.
Goals of the HITECH Act
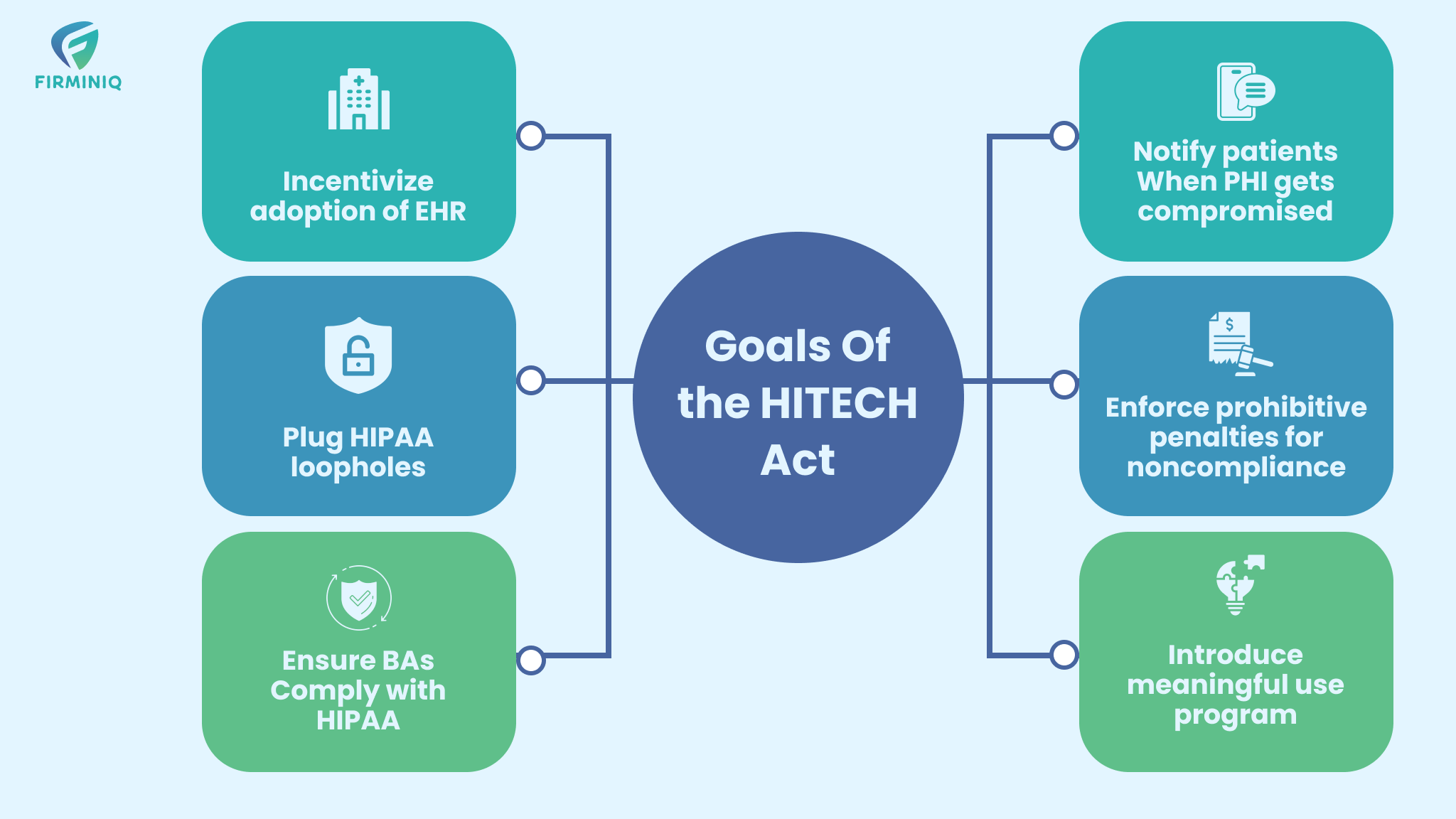
- Encouraging healthcare providers to adopt EHR systems.
- Closing gaps in HIPAA regulations.
- Ensuring that Business Associates of covered entities comply with HIPAA rules and regulations.
- Informing patients when their Protected Health Information (PHI) is compromised.
- Enforcing substantial penalties for HIPAA non-compliance.
- Enhancing the quality, safety, and efficiency of healthcare while adhering to HIPAA standards.
Key Components of the HITECH Act
- Business Associate HIPAA Compliance: The HITECH Act established strict requirements for Business Associates, including the enforcement of business associate agreements, higher penalties for non-compliance, and obligations for breach notifications.
- Willful Neglect and Auditing: The HITECH Act mandated security audits for healthcare providers and introduced a tiered system of penalties and fines for violations.
- Meaningful Use Program: Initiated by the Department of Health and Human Services (HHS), this program focuses on improving healthcare quality, safety, and efficiency while reducing health disparities.
Policies and Procedures – Core of HIPAA
Foundation of Compliance:
Policies and procedures are critical for meeting HIPAA’s Privacy, Security, and Breach Notification Rules. They provide a clear structure for managing PHI within an organization.
Risk Management:
By establishing comprehensive policies, organizations can proactively identify, assess, and mitigate risks associated with PHI, thereby helping to prevent data breaches and secure sensitive information.
Guidance for Workforce:
These policies offer detailed guidance for employees on securely managing PHI and complying with HIPAA regulations, including protocols for PHI disposal and breach response.
Consistency in Operations:
Standardized policies ensure that all employees adhere to the same procedures, reducing the likelihood of errors and inconsistencies in PHI management.
Audit Readiness:
Well-documented policies and procedures demonstrate to auditors that an organization is committed to HIPAA compliance and has taken necessary steps to protect PHI.
Key Components of HIPAA Policies and Procedures
Privacy Policies:
These policies specify how PHI should be used and disclosed, ensuring that access to sensitive information is limited to authorized individuals.
Security Policies:
Security policies address the technical, physical, and administrative measures needed to safeguard PHI, including encryption, access controls, and employee training.
Breach Notification Policies:
These policies outline the steps to take in the event of a data breach, including notifying affected individuals and authorities promptly.
Employee Training and Sanctions:
Include guidelines for training staff on HIPAA compliance and outline consequences for non-compliance, ensuring that all employees understand their responsibilities.
Incident Response Plans:
These plans detail the actions to be taken in the event of a security incident or breach, covering investigation, mitigation, and reporting.
Regular Review and Updates
Organizations need to consistently review and update their HIPAA policies and procedures to keep pace with emerging technologies and evolving regulations. This practice ensures continuous compliance and the protection of PHI.
Mapping HIPAA Requirements to AWS
Understanding the shared responsibility model between AWS and customers is essential for HIPAA compliance. The following is a guide on how to align HIPAA requirements with AWS services, specifying the responsibilities of both AWS and the customer:
1. HIPAA Administrative Safeguards
Security Management Process:
AWS Responsibility: AWS offers security tools like AWS Identity and Access Management (IAM) for managing user permissions.
Customer Responsibility: Customers must implement IAM policies, conduct risk assessments, and establish security policies within their environments.
AWS Tools: Identity and Access Management (IAM), AWS Organizations, AWS Config, and AWS Security Hub.
Workforce Security:
AWS Role: AWS secures its workforce by conducting background checks and providing security training.
Customer Responsibility: Customers manage workforce access to AWS resources and provide HIPAA-related training.
AWS Tools: Identity and Access Management, AWS Single Sign-On, AWS CloudTrail.
Information Access Management:
AWS Responsibility: AWS provides tools like IAM roles, policies, and Multi-Factor Authentication (MFA) for controlling access.
Customer Responsibility: Customers must implement and review access control policies within their environments.
AWS Tools: IAM, AWS MFA, AWS Directory Service, AWS CloudTrail, Amazon CloudWatch Logs.
Security Awareness and Training:
AWS Responsibility: AWS offers documentation and best practices but does not directly train customer staff.
Customer Responsibility: Provide HIPAA-focused training on secure AWS usage.
AWS Tools: AWS Documentation, AWS Training and Certification, AWS Well-Architected Tool.
Security Incident Procedures:
AWS Responsibility: AWS monitors its infrastructure and provides incident response.
Customer Responsibility: Customers must develop and implement their own incident response plans for their AWS environments.
AWS Tools: AWS GuardDuty, AWS Security Hub, AWS CloudTrail, Amazon CloudWatch.
2. HIPAA Physical Safeguards
Facility Access Controls:
AWS Responsibility: AWS is responsible for managing the physical security of its data centers.
Customer Responsibility: Manage access to devices that connect to AWS resources.
AWS Tools: Not applicable (handled by AWS).
Workstation Use:
AWS Responsibility: AWS services do not directly manage workstation use.
Customer Responsibility: Ensure workstations accessing AWS comply with HIPAA standards.
AWS Tools: AWS WorkSpaces, AWS Systems Manager.
Device and Media Controls:
AWS Responsibility: AWS provides secure storage options like Amazon S3.
Customer Responsibility: Encrypt data and ensure proper data disposal.
AWS Tools: Amazon S3, AWS Key Management Service (KMS), AWS Secrets Manager, AWS Storage Gateway.
3. HIPAA Technical Safeguards
Access Control:
AWS Role: AWS offers access control solutions like Identity and Access Management (IAM) and Multi-Factor Authentication (MFA).
Customer Responsibility: Configure and enforce access controls within your AWS environment.
AWS Tools: IAM, AWS Single Sign-On, Multi-Factor Authentication (MFA), AWS Secrets Manager, and Amazon Cognito.
Audit Controls:
AWS Role: AWS delivers logging features through services like AWS CloudTrail
Customer Responsibility: Enable and monitor logging, ensuring logs are stored securely.
AWS Tools: AWS CloudTrail, Amazon CloudWatch, AWS Config, AWS Audit Manager.
Integrity:
AWS Responsibility: AWS provides encryption tools like AWS Key Management Service (KMS).
Customer Responsibility: Implement integrity controls and validate data integrity using checksums.
AWS Tools: AWS KMS, AWS Certificate Manager (ACM), Amazon S3 Object Lock, AWS Lambda.
Person or Entity Authentication:
AWS Responsibility: AWS provides secure user authentication methods, including MFA.
Customer Responsibility: Ensure that users authenticate securely.
AWS Tools: IAM, AWS MFA, AWS Directory Service, AWS Cognito.
Transmission Security:
AWS Responsibility: AWS services support secure transmission protocols like HTTPS and TLS.
Customer Responsibility: Ensure data in transit is encrypted using these protocols.
AWS Tools: AWS Certificate Manager (ACM), AWS CloudFront, AWS Elastic Load Balancing, Amazon VPC.
4. HIPAA Breach Notification Rule
AWS Responsibility: AWS informs customers of any security breaches that impact their environments.
Customer Responsibility: Customers must implement breach notification procedures, including timely reporting to affected individuals.
AWS Tools: AWS GuardDuty, AWS Security Hub, Amazon CloudWatch, and Amazon Simple Notification Service.
5. HIPAA Privacy Rule
AWS Responsibility: AWS adheres to privacy practices in its service offerings.
Customer Responsibility: Ensure PHI is accessible only by authorized individuals within your AWS environment and enforce privacy policies.
AWS Tools: IAM, Config, Amazon Macie, Secrets Manager, Amazon S3.
Shared Responsibility in AWS:
AWS: Secures the infrastructure running AWS services.
Customers: Secure the data stored in AWS, manage access controls, configure security settings, and ensure HIPAA compliance within their applications.
By clearly understanding these shared responsibilities, organizations can effectively manage HIPAA compliance while utilizing AWS services. Regular documentation and auditing of controls are essential to ensure continuous compliance.