Client Background
A leader in medical device manufacturing for blood pressure and pain management. The company also provides healthcare solutions to enable healthcare infrastructure consisting of doctors, hospitals, patients, and healthcare support staff.
Project Overview
The primary requirement from the client was a platform that could handle high volumes of data and ensure safe processing of that data while complying with Health Insurance Portability & Accountability Act (HIPAA), California Consumer Privacy Act (CCPA), General Data Protection Regulation (GDPR), and ISO 27001 requirements. Our team of experts addressed the key challenges such as risk management, security controls, and identifying HIPAA-compliant services. We also improved the client’s security posture by implementing gap remediation activities, conducting policy reviews, and establishing a comprehensive cloud security policy. Additionally, we also helped with security incident monitoring and management and set up processes and practices for ISMS and risk management.
Business Requirements
- They needed a platform on AWS that could handle high volumes of data and ensure the safe processing of that data for them to be compliant with ISO 27001, HIPAA, CCPA and GDPR requirements.
- Platform is used by:
-
- 3M mobile app users worldwide.
- 100’s of remote patients monitoring hospitals for managing their thousands of patients across North America (NA).
-
Challenges
- Patient data is collected across NA from mobile app users or from hospitals providing remote patient monitoring.
- Client is dealing with the sensitive Personal Health Information (PHI) and Personally Identifiable Information (PII) of patients. Cloud infrastructure must comply with HIPAA and all the security guidelines and best practices.
- The client was looking for a team of experts that could help them set up and maintain a CI/CD implementation on AWS that fully complies with security guidelines.
- The client was looking for a secure environment that meets with security guidelines and infrastructure vulnerability scans.
- They partnered with us considering our proven expertise in AWS and DevOps and our AWS certified solution and security architects.
Challenges in achieving compliance
Compliance for healthcare is one of the most challenging domains and most organizations struggle when building IT based solutions on top of existing hardware solutions or implementing solutions that require the service provider to handle PII and PHI data.
- Key ISO 27001 Challenges
- ISMS (Information Security Management System): All the policies, procedures, guidelines and controls need to be in accordance with the requirements of ISO 27001.
- Risk management: Identifying assets, assessing threats and vulnerabilities and determining the likelihood and impact of potential incidents.
- Security controls: Implementing appropriate administrative, physical, and technical safeguards to protect PHI.
- Key GDPR Challenges
- Storage limitation: Implementing data retention policies are an outcome of storage limitation.
- Integrity & confidentiality: Personal data must be processed to ensure protection against unauthorized or unlawful processing and against accidental loss, destruction, or damage.
- Key HIPAA Challenges
- Acquiring a BAA (Business Associate Agreement):It can be challenging to ensure that all parties have a clear understanding of the requirements and responsibilities outlined in the BAA, and that business associate is willing to assume certain responsibilities or liabilities.
- Identifying and choosing HIPAA-compliant services/service providers: All service providers are required to be independently assessed for compliance, monitored and their sustained compliance ensured.
- Conducting regular risk assessments: HIPAA requires healthcare organizations to conduct regular risk assessments to identify and address potential security vulnerabilities.
- Implement Disaster Recovery (DR) plan: To ensure the availability and integrity of PHI in the event of a disaster or outage, organizations are required to implement and maintain a DR plan.
Solution
Security Posture Improvement
We identified & addressed various security gaps through the implementation of security processes, policies, cloud native tools, and operational procedures. This led to a significant improvement in the client’s security maturity ranking across over 200 evaluation measures. Additionally, a comprehensive cyber security strategy plan was developed, taking into account the business objectives and priorities of relevant stakeholders. A cloud security policy was established to guide the implementation of critical security controls. Furthermore, the supplier security risk management capability was enhanced through detailed security questionnaires, which provided insights into the security posture of third-party vendors. Any identified security gaps were promptly addressed through remediation efforts, ensuring a secure vendor ecosystem for the client.
Security Incident Monitoring & Management
We implemented security measures such as static code scans for cloud applications, established a security incident management framework, and collaborated with a system integrator to implement a cloud-native security monitoring solution. A 24/7 Network Operations Team was set up for efficient handling of alerts and incidents and cloud incident response runbooks were created for faster incident assessment and containment.
Process and Practices
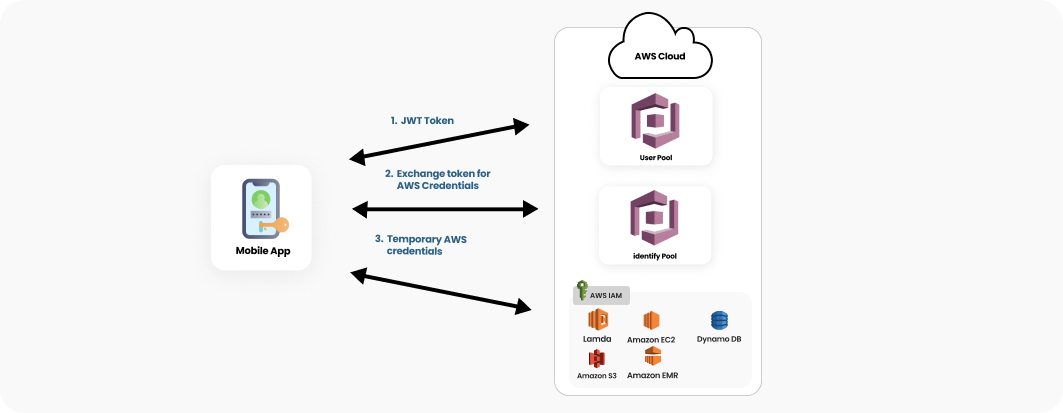
We established a process for regular training and tracking of ISMS policies. We also implemented risk management practices by maintaining up-to-date inventory and asset details. Our AWS security experts helped set up AWS services like CloudTrail and CloudWatch to ensure compliance with client and regulatory guidelines and proactively identify any security gaps.
Security Implementation Done Right
Our certified security team ensured optimal implementation of AWS security features, meeting or exceeding security requirements while considering cost and ease of maintenance. We leveraged AWS security features like IAM, SSO, AWS Config, Security Hub, WAF, encryption, and network security to help the healthcare organization meet compliance standards. We secured production workloads with least privileged access, fault-tolerant VPN tunnels, and restricted infrastructure access. Physical and technical safeguards, such as biometric access control and encrypted workstations, were implemented. Internal audits and regular automated risk assessments were conducted using AWS services. We also implemented appropriate security controls and optimized AWS services for cost and efficiency.
Enabling GDPR Specific Compliance
We helped the client achieve GDPR-specific compliance by evaluating storage limitation statutes and implementing data retention policies using AWS features like Amazon S3 Lifecycle, AWS Backup, and DynamoDB tables. Our team simplified the compliance process by leveraging AWS’s HIPAA-compliant BAA. FIRMINIQ’s DevOps team planned and implemented a disaster recovery plan tailored to the client’s business requirements, conducting periodic “Dry Runs” to ensure its effectiveness.
Results
Successful Implementation of Security Processes and Policies
FIRMINIQ’s security team identified gaps and implemented remediation activities resulting in a significant improvement in the client’s security maturity ranking. We also developed a comprehensive cyber security strategy plan and established a cloud security policy to prioritize critical cloud security controls. Additionally, we uplifted supplier security risk management by providing detailed security questionnaires to identify and remediate security gaps in the vendor ecosystem.
Strengthened Cloud Security
We implemented various initiatives to strengthen cloud security, including implementing static security code scans, establishing a security incident management framework, collaborating to implement a cloud-native security monitoring solution, establishing a 24/7 Network Operations Team, and producing cloud incident response runbooks with conditional steps. These measures ensured secure and trustworthy software systems, efficient incident response, better threat analysis, adherence to security requirements, and accelerated assessment, investigation, and containment of incidents.
Information Security and Risk Management
FIRMINIQ implemented an ISMS training process to keep the team up to date with policies and ensure changes are communicated systematically. We also prioritized risk management by maintaining up-to-date inventory and using AWS services like CloudTrail and CloudWatch to ensure compliance and highlight potential security lapses.
Thorough Compliance
We helped the client comply with GDPR storage limitations by deploying data retention policies and utilizing AWS’s built-in retention features. We also simplified the compliance process by providing a HIPAA-compliant BAA for the healthcare client. Additionally, we implemented an efficient disaster recovery plan.
Tech stack
AWS services
Application Integration
Compute
Database
Management & Governance
Security, Identity, & Compliance