ISO 27001 stands as a cornerstone in the realm of security standards. It delineates the recommended requisites for erecting, overseeing, and enhancing an Information Security Management System (ISMS). An ISMS comprises a set of policies devised to safeguard and administer an enterprise’s sensitive information, spanning from financial data and intellectual property to customer particulars and employee records.
ISO 27001 functions as a voluntary benchmark embraced by service providers aiming to fortify customer information. Compliance mandates an independent, accredited body to conduct formal audits on organizations, ensuring adherence to the standard.
Benefits of Partnering with an ISO 27001 Certified Service Provider
Partnering with an ISO 27001 certified service provider yields manifold benefits:
1. Risk Management: Through an ISMS, an organization regulates access to specific information, thereby mitigating the risk of data theft or compromise.
2. Information Security: Protocols within an ISMS delineate the handling and transmission of data, bolstering information security.
3. Business Continuity: Sustaining ISO 27001 compliance necessitates perpetual testing and enhancement of an ISMS. This proactive approach averts data breaches that could jeopardize core business operations.
For service providers, compliance not only engenders trust among customers but also underscores a commitment to robust data security practices.
Integration of ISO compliance into information security governance is pivotal. This governance encompasses the plans, tools, and business practices employed by an enterprise to safeguard sensitive data.
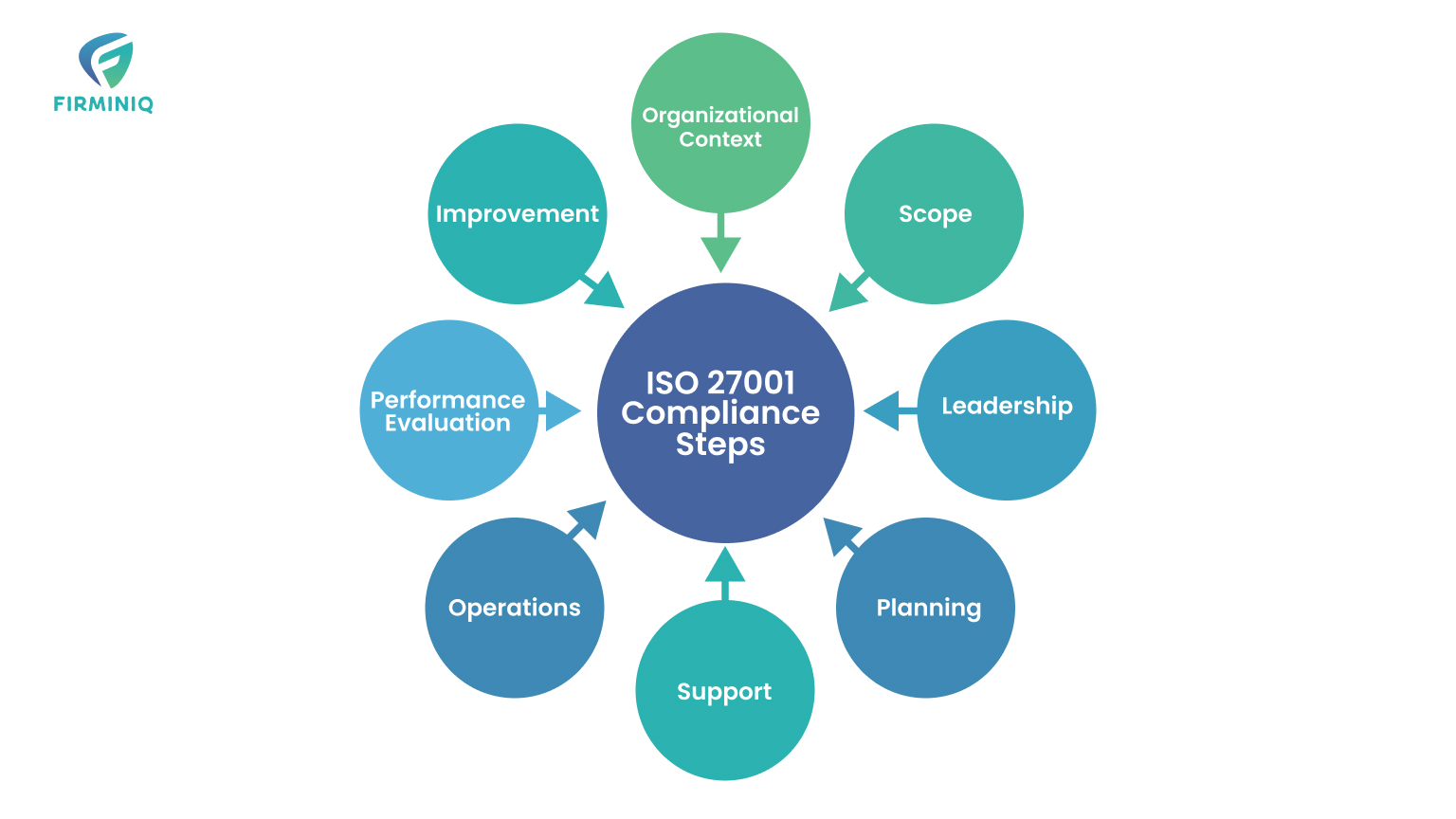
Key Elements of Achieving ISO 27001 Compliance and Establishing an ISMS
Achieving ISO compliance and establishing an ISMS entails a comprehensive process, encompassing scoping, planning, training, and support. Key elements include:
1. Organizational Context: Identifying internal and external factors influencing ISMS development, including legal, regulatory, and contractual obligations.
2. Scope: Documenting the scope of the ISMS based on identified factors, delineating relevant areas and boundaries. Integration into the overall management structure is emphasized.
3. Leadership: Management must exhibit leadership by aligning the ISMS with organizational strategy, communicating its importance, and fostering continual improvement.
4. Planning: Developing a risk management plan, including risk analysis, treatment, and mitigation strategies.
5. Support: Securing resources, training, and infrastructure for ISMS implementation, while fostering employee awareness and communication policies.
6. Operations: Executing planned processes, documenting actions, and controlling outsourced processes to manage information security risks.
7. Performance Evaluation: Conducting internal audits and management reviews at defined intervals to assess ISMS performance and identify areas for improvement.
8. Improvement: Promptly addressing nonconformities, executing corrective actions, and continually enhancing the effectiveness of the ISMS.
In summary, ISO 27001 serves as a guiding framework for organizations committed to fortifying their information security posture and fostering a culture of continuous improvement.